Cloud-Based Advanced Spam Filter
- Stop spam before it reaches your domain
- unlimited email addresses
- Never miss an important email
- Configurable protection
- Heuristic learning (ie new attacks are anticipated)
- 30 day email archiving
- Enterprise solution available with ProofPoint technology
Built with Microsoft 365 and G Suite in mind
100% configurable for your company needs
Tracking 100+ million senders
Sender behaviors are tracked in real time. The sender's reputation is weighed during the filtering process.
Thousands of filters added daily
Using spam traps around the world we are able to detect new spam attacks as they occur and adapt to them instantly.
Searchable Quarantine
Never miss an important email. All spam is stored in a searchable quarantine.

Easy set up
The process usually takes less than 5 minutes to get set up! In fact, you don’t even have to tell us what email addresses on your domain are valid. During your trial period, our heuristic scanners will auto-learn what email addresses on your domain are valid.
Remarkable accuracy
Unlike other spam filtering systems that rely on fancy algorithms that spammers can easily defeat, Our rule based system features million of rules that are constantly updated and maintained by spam techs 24/7

Zero-Hour Virus Protection
Like other spam filtering solutions, we use popular virus scanners to help block viruses. These scanners do catch some viruses, but we have added our own detection systems that watch for patterns and automatically block new viruses hours before commercial virus scanners have been updated.
Almost ZERO false positives
A “false positive” is when a good email is blocked by a spam filter. While other spam filters use automated systems to “auto-learn” spam, a process that is prone to errors, Our rules are carefully engineered to ensure that only real spam is
blocked - and they are configurable too

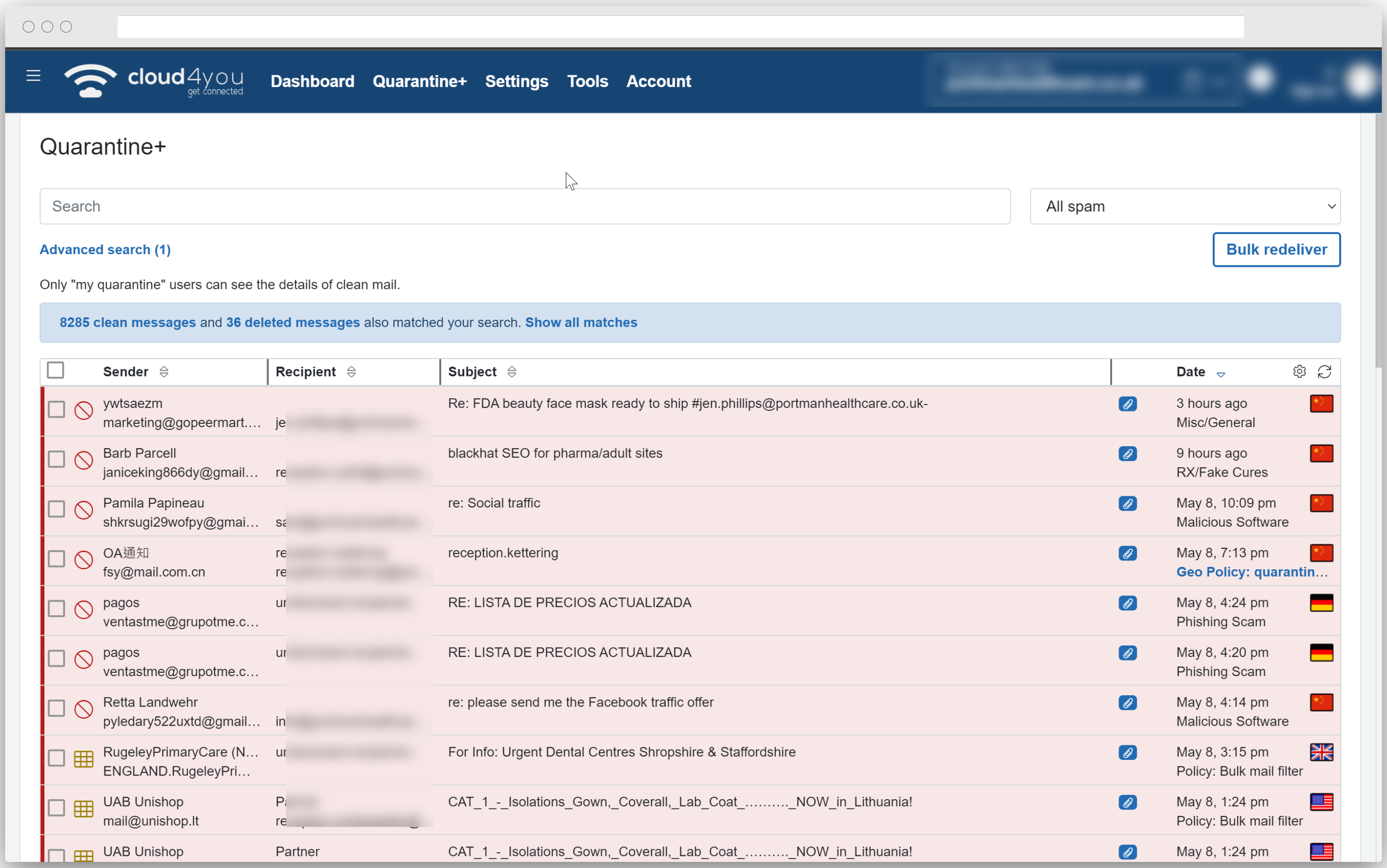
Quarantine viewer included
Rather than just deleting spam that is blocked, all spam is placed in an easy-to-use domain-wide quarantine where it can be viewed by you, further ensuring that no good email is ever lost. Optionally, you can set up a separate quarantine for each user on your domain and enable spam reports, decreasing the overhead in your Service Desk.
Reliable cloud based filtering
Our geographically diverse cloud based filtering runs on hardware that we own and manage. Or, to explain it without the cliche terminology, every customer domain is assigned to redundant servers in multiple geographical locations to ensure reliable email delivery.

Whole domain filtering at one low price
Other services charge extra for every email address on your domain, or require you to set up a separate subscription for each of your domain aliases. With us there really is no limit!*
Automatic mail spooling
If your mail server goes down, our service will automatically hold your clean messages until your mail server is back online. Mail is automatically held for up to 30 days.


Smart and friendly support
All support emails are answered same day and we aim to resolve your problem immediately
Access to message logs
We provide 30 days of delivery logs for each clean message so that if a message goes missing, you can easily track it down.


URL Defence from ProofPoint and Malware Sandboxing
Targeted email attacks containing malicious links represent one of the most dangerous IT threats facing enterprises today. We partnered with ProofPoint to offer their comprehensive email analysis solution for combatting targeted threats using a full lifecycle approach, monitoring suspicious messages containing malicious URLs or malicious attachments, and observing user clicks as they attempt to reach out.
We leverage the advanced power of Targeted Attack Protection from Proofpoint’s industry leading email analysis solution in order to provide enterprise level protection to effectively detect malicious attachments.
Advanced Malware Detection Attachment Defense uses the visibility and intelligence gathered from analyzing the email of many of the largest companies in the world and applies this to smaller enterprises. This gives SME’s an advantage of scale and security utilizing the capabilities of Cloud4You, without having to dedicate resource to managing the system manually.
The email attachment filtering capability leverages dynamic sandbox technology that powers the our Targeted Attack Protection solution. Intelligence gathered by the dynamic malware analysis is used to identify and block malicious attachments that are designed to evade traditional security solutions. These attachments, such as Microsoft Office documents, are often used in spear-phishing attacks, to deliver banking Trojans, ransomware, or other malware. Cloud4You Advanced Spam Filter ensures all aspects of email attachment filtering meets the security, availability, and resiliency needs of the smaller enterprise.
Protect your business against advanced threats in email with malicious attachments and URLs – even zero-day, polymorphic malware, weaponized documents, and credential phish.
Dynamically analyse and block in real-time the malicious URLs and attachments that can evade antivirus and reputation filters to deliver banking Trojans, ransomware, and other malware.
Detect sophisticated malware attacks, including:
- Polymorphic and zero-day malware
- Malicious attachments
- Other advanced exploits
In order to detect such advanced malware effectively—whether malware spread via spear-phishing emails containing a malicious attachment, watering hole URLs over email, or longline phishing campaigns — our malware analysis system technology uses a combination of sophisticated techniques to evaluate advance threats, including:
- Real-time checks against emerging campaigns and new malicious websites that are being detected across organizations
- Static code analysis that looks for suspicious behaviour, obfuscated scripts, malicious code snippets, and redirects to other malicious sites
- Dynamic malware analysis that sandboxes the destination URL or suspicious attachments to simulate a real user on a machine, with the goal of observing any changes made to the system
Our anti-evasion technology, in the dynamic analysis, tricks malware into revealing itself by creating virtual environments that accurately reproduce real system and real user behaviour and interactions. This process provides comprehensive detection analysis that determines whether the destination URL or an attachment under suspicion is malicious, even finding malware that is sophisticated enough to conceal itself from detection leveraging techniques, e.g., IP rotation, mouse movement simulation, real browser sessions, time-delayed analysis.
We leverage cloud-based Big Data analytics to predictively detect malicious URLs in unsolicited emails and block user clicks before they can lead to a compromise.
Our filter applies machine-learning heuristics to model email flow at a per-user level, and at a cloud-level across all traffic within Targeted Attack Protection, in order to block URLs even before they host active malware, using a cloud-based process that incorporates Big Data techniques and a real-time scoring engine, including:
- Anomaly tics Service
- Kill Chain Analysis and Pre-emptive Sandboxing
Together, these technologies provide the ability to predictively determine what could likely be malicious—and take pre-emptive steps before any user has a chance to click and have their machine compromise.
Depending on your needs we have two licensing modules, per domain or per mailbox.
To use our URL Defence and Sandboxing powered by ProofPoint you need o signup for the “per mailbox” licensing module
Depending on your requirements you can have your whole domain protected for all your mailboxes for as little as £30/month. Talk to us to discuss your business needs